In this article, we will configure UNAT in Palo Alto Firewall. UNAT NAT is a special type of NAT which is configured when internet users want to access internal servers using their public IP address. Here, in this case, we have to configure UNAT. UNAT is also known as U-Turn NAT. So, let’s configure!

Scenario: An Example for UNAT for DMZ Servers
In this example, I’ve configured three different zones on the Firewall, i.e. INTERNET, LAN, and DMZ. ISP is connected to the ethernet1/1 which is in the INTERNET zone. LAN segment is connected to the ethernet1/3 and DMZ is connected to the ethernet1/2. Now, the requirement is to access the DMZ Zone servers from the LAN segment. But, the LAN users will only use the public IP address of the DMZ Servers.
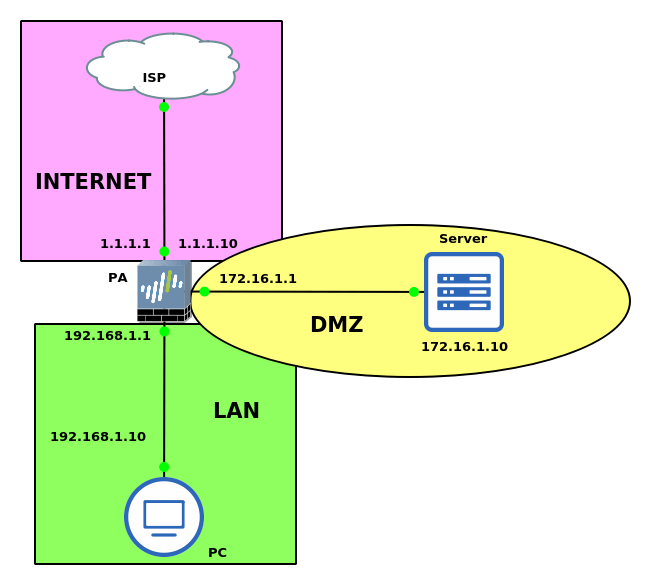
The DMZ server has an IP address 172.16.1.10. A Public IP address 1.1.1.10 is DNATed with this server. So, traffic on this public IP from the internet will be forwarded to the DMZ server i.e. 172.16.1.10. Now, the LAN users will hit on public IP 1.1.1.10 and they will access the DMZ server using UNAT.
How to configure UNAT on Palo Alto Firewall
Configuring the Zones on Palo Alto Firewall
Let’s start the configuration by configuring the Zones on the firewall. Go to the Network >> Zones and click on Add. Now, provide the user-friendly name to the zone and select the type as layer 3. In my case, I’ve created 3 different zones i.e. INTERNET, LAN, and DMZ.
Configuring the Interfaces on Palo Alto Firewall
Now, we will configure the Firewall Interfaces. Access the Network >> Interfaces >> Ethernet and select the interface you want to configure. For example, click on ethernet1/1, select the type as Layer 3. In the same configuration window, select the virtual router and zone for this interface. In this example, the ethernet 1/1 interface is connected with the ISP and the default router and zone is default and INTERNET respectively. You need to configure the rest of the two interfaces as well.
Configuring the NAT policy for UNAT
In the simple DNAT scenario, we just create a NAT rule in which we have the same Source and Destination Zone. So, traffic from the INTERNET zone will hit a Public IP which is also in the INTERNET zone. So, as per the security policy, the traffic will be destinations to a specific server. A simple DNAT rule we configured like the below scenario:
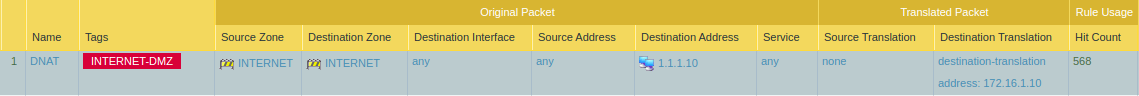
But, In UNAT, we have to choose different Source and Destination zones based on our traffic. In this example, my source zone will be LAN, but the destination zone will be the INTERNET. We can also specify the source addresses, but we will configure it as any. In the destination addresses, we have to define the public ip of the server. We also have to configure the Destination NAT as well, so select the Destination address as well. Go to the Policies >> NAT and click on Add.
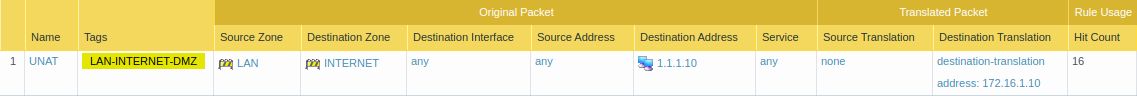
Configuring the Security policy for UNAT traffic
For simple DNAT Rule, we configure security rule by putting Pre NAT IP and POST NAT Zone. The source zone for the DNAT traffic will be the INTERNET and the destination zone will be the DMZ. But, still, the destination address will be the public ip reserved for the DMZ server. So, our policy for DNAT Traffic will be looks like the below scenario:

Now for UNAT Security Policy, the source zone will be the LAN and the destination zone will be the DMZ. We can specify the source address but the destination address will be the Public IP address of the DMZ server, i.e. 1.1.1.10 in this example. Here, I only allowed ping and ms-RDP applications.

Verification of UNAT configuration
Now, we have finished the UNAT configuration. We will test our configuration by accessing the DMZ server using the associated public IP. I just logon on to one of the hosts on the LAN segment. Now, I’ll initiate the ping to 1.1.1.10 (Public IP of DMZ server). As you have seen in the security policy, I enabled RDP on DMZ Server. So, I’ll also try to connect the DMZ server on port 3389, but using its Public IP address.
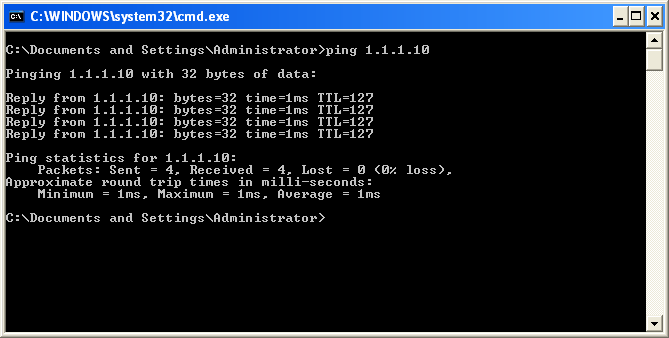
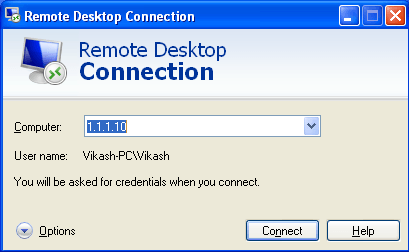
Ping from LAN to DMZ Server (Using DMZ server’s Public IP)
I just open the command prompt from the Windows machine and initiate a ping to the DMZ server using its public IP address. I can ping to the public IP address and following the result.
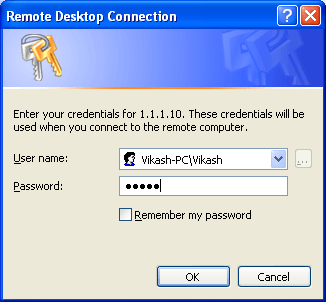
RDP from LAN to DMZ Server (Using DMZ server’s Public IP)
Now, as defined in our security policy, I have enabled the RDP on the DMZ server. I’ll open the RDP client and hits the public IP of the DMZ server. Here, I also able to access the DMZ server using its Public IP address.
Monitor the logs on the Palo Alto Firewall
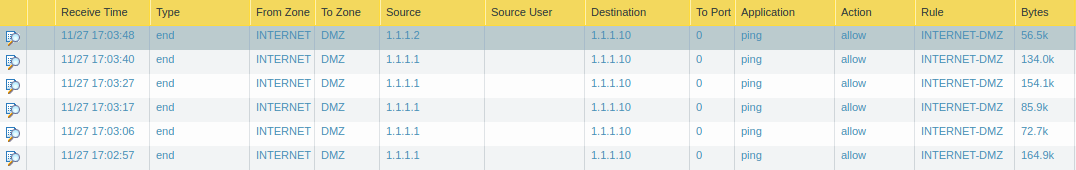
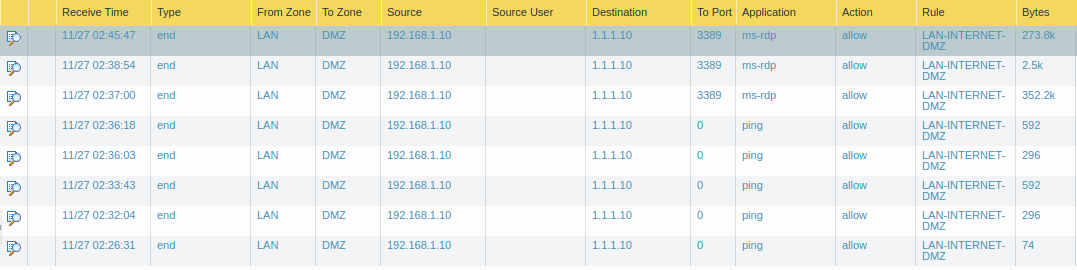
I have configured two NAT and Security Rules. The first one is the simple DNAT rule which allows access to the DMZ server using its public IP address. Another rule is the UNAT rule which allows the traffic from the LAN segment, but it changes the logical path of the traffic. First traffic will go to the INTERNET zone and then the firewall will re-route the traffic to the DMZ security zone.
Logs for DNAT Rule
Logs for UNAT Rules
References
Related Articles
- What is Network Address Translation | Different types of NAT
- SNAT vs DNAT | Source NAT vs Destination NAT
Summary
In this article, we configure UNAT on Palo Alto Firewall. UNAT allows you to re-route the logical path between different zones of the firewall. UNAT is used when internal users want to access Internal servers but use servers’ Public IP addresses. After configuring the UNAT LAN segment traffic first goes to the INTERNET zone. After, the same traffic will be re-routed to the DMZ security zone.
Did you like this article? If you have any questions or configuration related challenges just put a comment in comment box!
Thanks for the information.