In this article, we will discuss the Palo Alto Networks Deployment modes. We can deploy the Palo Alto Networks firewall in 4 different modes, i.e., TAP, V-Wire, Layer 2, and Layer 3. We will further discuss all of the Palo Alto Networks modes in detail. Let’s start!
Palo Alto Networks Firewall deployment modes
1. Palo Alto TAP Mode
Palo Alto Networks TAP mode is used for the Evaluation and Audit of existing networks. In the TAP mode, we can deploy the Palo Alto Networks Firewall in the customer environment, and we will have the visibility of Applications, Threats, and User ID information of the customer environment.
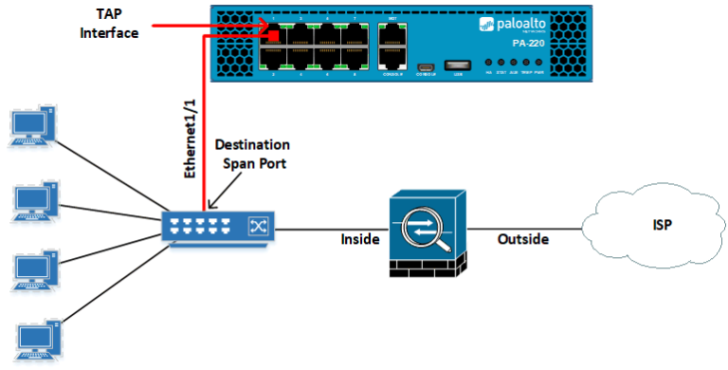
We usually use a SPAN/Mirror Port on the switches to forward the traffic to the Palo Alto Networks Firewall.
In TAP mode, we can’t control the traffic or threats that are traversing into the network. Also, we don’t need to assign IP Addresses to the firewall.
Since the TAP mode is widely used for POC purposes, we can generate the Stat Dump file from the Palo Alto Networks firewall and can generate a comprehensive report from the support portal.
To generate the stat dump file, just log in to Firewall and navigate to Device > Support.
2. Palo Alto V-Wire Mode
In V-Wire deployment mode, the Palo Alto Networks Firewall deployed inline with the existing network. We can configure a bundle of two different physical or virtual interfaces, and pass the traffic through them.
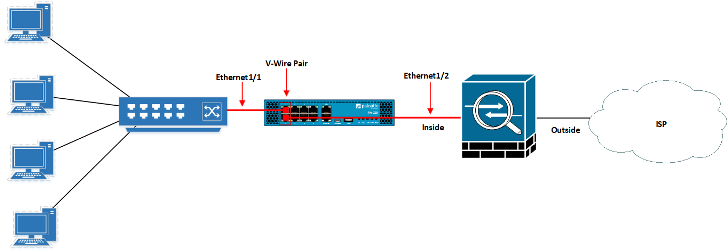
In V-Wire mode, we can deploy the firewall without changing the network topology. Since the firewall is placed in between the existing devices, we can easily control the traffic using security policies.
We will have complete visibility & control of Applications, Threats, and User-ID information. We can also perform SSL Decryption on the Palo Alto Firewall.
Like TAP Mode, we don’t need to assign IP Addresses in V-Wire mode.
3. Palo Alto Layer 2 Deployment Mode
Palo Alto Networks Layer 2 deployment provides Traffic Isolation on OSI Layer-2. We can have the different hosts connected on different layer 2 interfaces within the same network subnet. In this scenario, you can control the traffic between these hosts. You may also apply the App-ID, Content-ID & User-ID in the same setup.
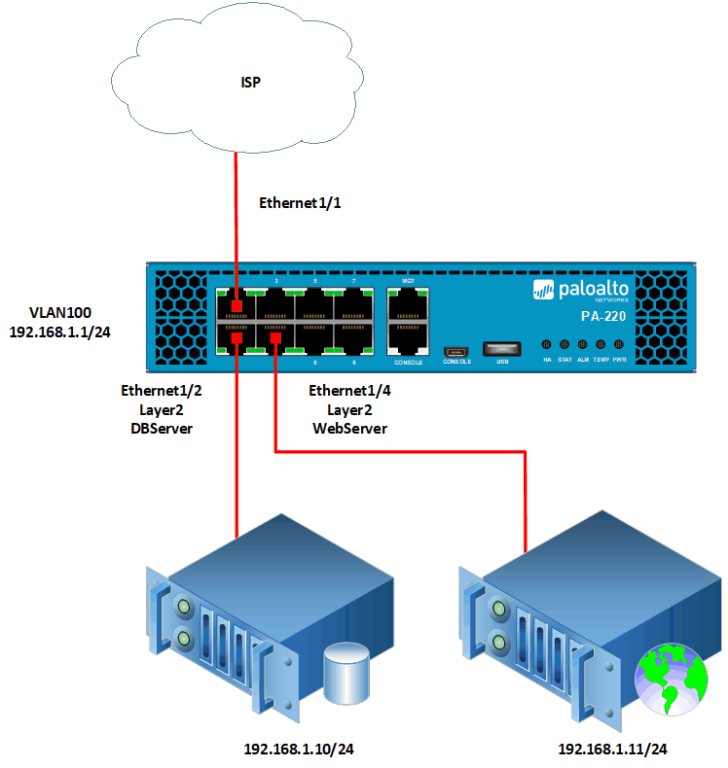
You may further assign the VLAN interface to the Layer 2 interface and perform the routing as per the requirement.
Like the TAP & V-Wire deployment, we can’t assign IP Addresses on the Layer 2 interface. However, the VLAN interface requires an IP Address & the Virtual Router to perform the routing.
4. Palo Alto Layer 3 Deployment Mode
This is the most common Palo Alto Networks deployment. Here, we need to assign IP Addresses on the physical and virtual interfaces. If the customer has an existing firewall in their environment, they need to migrate it to the Palo Alto Networks Firewall.
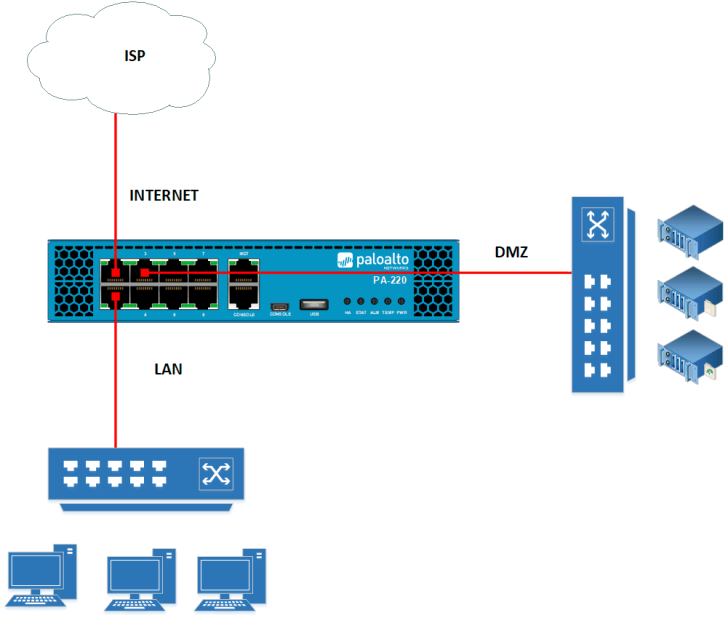
We can use AppID, ContentID, UserID, Routing (Static & Dynamic), SSL Decryption & VPN in Layer 3 deployment. Additional features, such as DHCP work on the Layer 3 mode.
Related Articles
- How to Configure GlobalProtect VPN on the Palo Alto Firewall
- Static Routing: Everything you need to know
- How to configure Palo Alto Networks Firewall as a DHCP Server
- How to Generate Self-Signed Root CA certificate in Palo Alto Firewall
- How to configure Clientless VPN on Palo Alto Firewall
- How to Configure Static Route on Palo Alto Firewall
- OSI Model – 7 Layers Explained in detail
Summary
In this article, we have discussed Palo Alto Networks Firewall deployment modes. We can deploy an individual interface in TAP, V-Wire, Layer 2 & Layer 3 modes. TAP mode is mostly used for evaluation purposes. We can’t control anything in TAP mode. In V-Wire Deployment, we deploy the firewall in transparent mode and we can control the traffic and can use SSL Decryption. We can use only the Routing, VPN (SSL/IPSec), GRE Tunnels, etc. on the Layer 3 deployment.
In the coming articles, we will deploy the firewalls in all of the deployment modes. Meanwhile, please share your thoughts in the comments.