Hi Guys! In this article, we will discuss how you can deploy the FortiGate Virtual Firewall in VMWare Workstation. You must have to download FortiGate virtual Firewall ovf file from your Fortinet support portal. In this scenario, we will configure the Virtual FortiGate Firewall in Linux as well as Windows environment. Before starting, it’s required you have a minimum of 4GB of RAM with an i5 or i7 processor. So, let’s start!
Also Read: How to deploy FortiGate VM Firewall in GNS3

Step 1: Download FortiGate Virtual Firewall
First of all, you have to download your virtual FortiGate Firewall from your support portal. To do this, visit here, and go to Download > VM Images > Select Product: FortiGate > Select Platform: VMWare ESXi as per the given reference image below. By default, you did ‘t get any license associated with your virtual image. So, you have to buy the licenses as per your requirements.
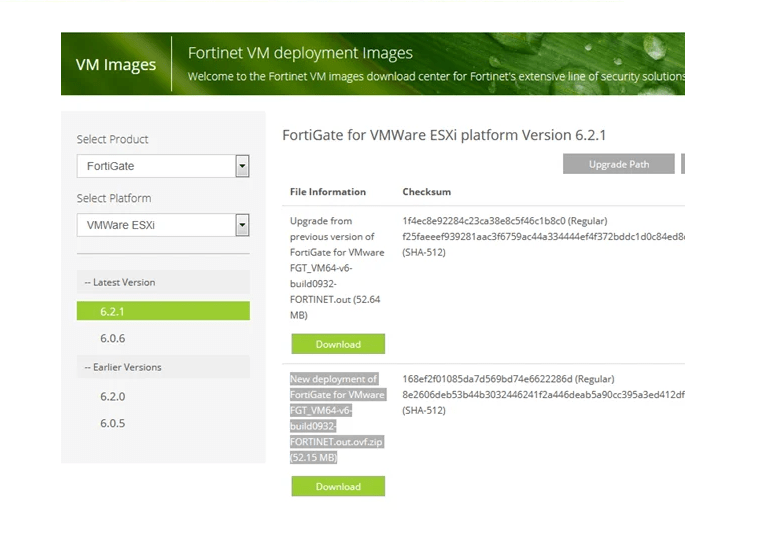
Image Source: Fortinet
After downloading, FortiGate VM Compressed file, you need to extract the files in a folder. Just use your Extract tool to extract the zip file and it looks like the below image.
Step 2: Download and Install VMWare Workstation
After downloading the Virtual Firewall image, you must have to download and install VMWare Workstation. If you already installed it, just skip this step. To download VMWare Workstation, visit the official website VMWare Workstation. By default, you get 30 days evaluation period, after that, you can purchase it. Once you have installed it, it will be looks like the below image:
Step 3: Configuring your Virtual Network Interfaces for FortiGate Firewall
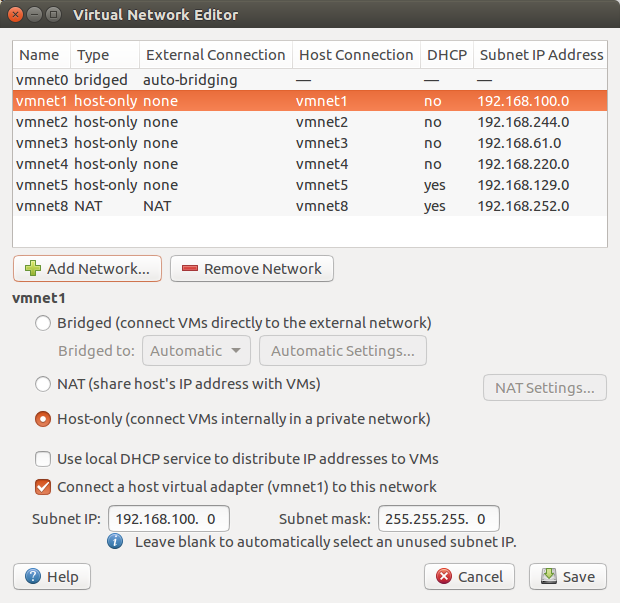
Now, it’s time to configure your Virtual Network Adaptors as per your requirements. By default, there are only two virtual network interfaces, i.e., VMNet1 and VMNet8. So, click on Windows Start Button and search for Virtual Network Editor. If you are using Linux (i.e. Ubuntu, Mint, etc.) you can type the below command to open Virtual Network Editor. Click on the Add Network and make your virtual interface host only. After that, you have to provide the IP address. For example, I am going to use 192.168.100.0/24 for the vmnet1 interface.
[terminal]sudo vmware-netcfg[/terminal]
Step 4: Deploying the FortiGate VM Image in VMWare Workstation
Now time to deploy the FortiGate virtual firewall in VMWare Workstation. Just open the VMWare Workstation and go to Files >> Open (Ctrl+O). Select the ovf file you have download from the support portal. This process will take some time, so have patience. After the successful completion of this process, just modify the assigned virtual network interfaces, memory, and processor. In my case, I’m giving 2GB RAM, 2 Processors, and 4 different virtual network interfaces (VMNet1, VMNet2, VMNet3, VMNet4). Let’s change the Firewall resources by clicking on Edit virtual machine settings. You can check the below images for reference.


Step 5: Configuring the Management Interface of FortiGate VM Firewall
Now, we have just finished the process of deploying the FortiGate firewall in the VMWare Workstation. Now you have to configure an IP address to the Management Port. The first virtual interface will be the management interface. So, assign an IP address in the same range as we assigned in Step 3. This is the first look when you press the power-on button.
Hint: The default username is admin and password is [blank].
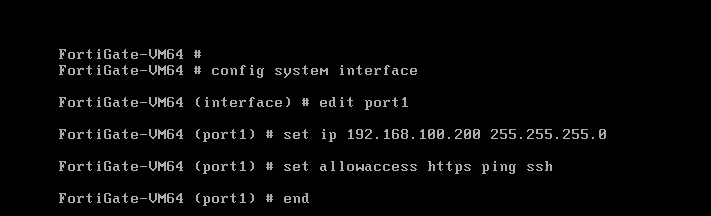
To assign the IP address, you have to follow the given commands:
[terminal]config system interface[/terminal]
[terminal]edit port1[/terminal]
[terminal]set ip 192.168.100.200 255.255.255.0[/terminal]
[terminal]set allowaccess https ping ssh[/terminal]
[terminal]end[/terminal]
Step 6: Accessing the FortiGate VM Firewall using GUI (Graphical User Interface)
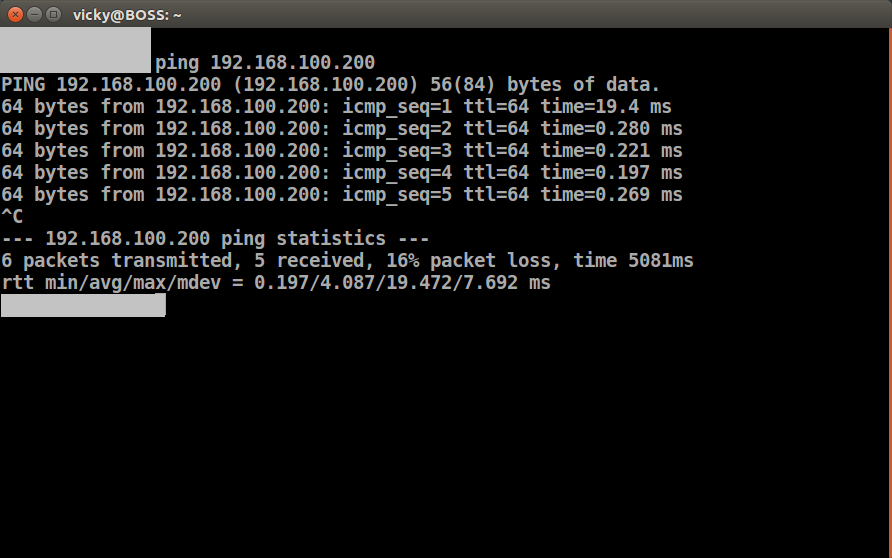
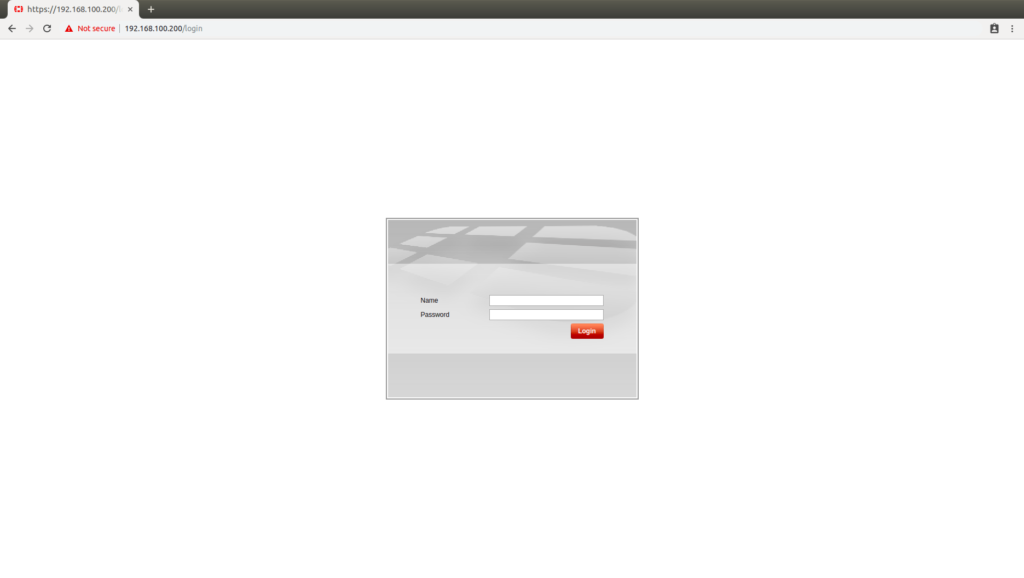
Now, it’s time to testing our configuration and accessing the FortiGate firewall using GUI. To do this, first, we will check the connectivity to our Firewall using the ping utility. After this, we will access the FortiGate Firewall GUI using its management interface IP address.
Default username is admin and password is [blank].
Related Articles
Summary
In this article, we have discussed how we can deploy the FortiGate Virtual Firewall in the VMWare workstation. It is required that you have a minimum of 4 GB of RAM and an i5 or i7 processor to deploy FortiGate in VMWare. If you have any difficulties in deploying the firewall in VMware, you can comment in the comment box!
Did you found this article helpful? Please comment your views in the comment box!
how to fix Access to 192.168.189.110 was denied
You don’t have authorization to view this page.
HTTP ERROR 403
Please allow the HTTP access to that particular interface. You just need to use below command:
“set allowaccess http https ping ssh”. Please Let me know if this not fix your problem.
You don’t have authorization to view this page.
HTTP ERROR 403. Allowd http https ping ssh telnet. Able to ping but able to do ssh or http or https
Hi Praveen, by default, an HTTPS certificate prevents you to take GUI of the firewall. As you already allowed the HTTP, first try to open the FG Firewall using http:// in private/guest window. Second, make sure you get ping response as ttl 255 or 254. If you receive a ping from any other value, maybe you configured this IP on different devices/appliance.
Please let me know if you still getting the issue.
Hi Admin, I followed your instruction to the end and I’m able to ping and ssh the fortigate, I just can’t access it via the gui using my designated IP address. I tried both http://192.168.0.40 and https://192.168.0.40 to no avail. I’m a little stuck and would appreciate any help
recreated the VM after that everything works fine
Fine Praveen!
I hope you like this article. Please share it on social platforms like Facebook and helps us.
first command: configure system interface_it’s always show unknown action 0, why?
Hi Pheak,
Please try with the “config system interface” and let me know if this resolve your issue.
I want the pc in vmware to connect to this fortigate also different port on fortigate. what should i do ?
Please, anyone, reply to me.
I have followed every step in you guide but I can not ping the fortigate . is there any special procedure on choosing ip addresses.
I connected port1(192.168.100.10) to VMnet1(192.168.100.101). But I don’t get connection between them…Please solve it…..
Hi Cthunder, Did you allow access on this particular port using the set allowaccess command?
Youa re still killing it in March 6, 2022. It worked for me thank you… didn’t know I had to set access for ping too
HI Team,
I followed above steps and I set the Fortigate VM IP as 19.168.20.10/24
Assigned the same subnet(192.168.20.0/24) for Virtual editor and my system has taken below IP address
Ethernet adapter VMware Network Adapter VMnet2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::9c9b:df1a:26b3:96c4%8
IPv4 Address. . . . . . . . . . . : 192.168.20.1
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
When i try to ping got destination host unreachable, and not able to configure TCP/IP4 settings as well. , Could someone Pl help me on this
Hi Jamy17, you mentioned that you set IP address 19.168.20.10/24, so, first correct the IP Address. Make sure VMNet2 is connected to the same interface of FortiGate where you assigned IP address. Further, you need to allow the access using set allowacess command.
Hi Admin,
Thanks for your quick reply
The IP address is 192 and not 19 that was typo.
i have already did set allowaccess ping https http ssh and when i ping 192.168.20.10 again still getting the same error
1st packet reply “destination host unreachable” and
rest “request timed out”.
Did i miss anything with the adapter settings !!!
Hi admin, how are you?
same problem as Jamy17
i have already did set allowaccess ping https http ssh and when i ping 192.168.192.100 again still getting the same error ” destination host unreachable”.
I was try to connect but it’s show “Evaluation license has expired. Upload a new license.” How to fix this error ?
Hi Admin
How to activate trail license..
Requesting FortiGate evaluation license message coming.. after some time dns resolve error. How to solve this?
When I want to download Fortigate FW v7 in VMWARE Workstation.I did the same commands but after typing configure system status I get lincence status : invalid from the first day,