In this article, we will discuss SSL Decryption Palo Alto Next-Generation Firewall. By default, encrypted web (i.e HTTPS) traffic passes through the firewall. So, a firewall administrator doesn’t come to know what will be inside of the encrypted traffic. So, if you want to inspect the inside of the https header content, you have to decrypt the encrypted web traffic. Let’s get started!

What is SSL Decryption – Palo Alto NG Firewall
As discussed above, SSL Decryption is the ability to read the HTTPS traffic content. By default, whatever traffic comes over the HTTPS, we don’t have any idea of its inside traffic. For example, it is very easy to send malicious content or command & control traffic over HTTPS. So, whenever this traffic comes to the firewall, the firewall simply forwards the packet towards the destination, because the traffic is totally encrypted. Therefore, if you want a deep analysis of HTTPS traffic, you should go for SSL Decryption. After the SSL Decryption, it is very easy to find the applications used in your network.
How SSL Decryption Works on Palo Alto Firewall
Normally, there is SSL Handshake happens between the client system to the web server whenever a system tries to access the webserver over HTTPS. The SSL Handshake is similar to the TCP Three-way handshake. Here, both client and server machines exchange their certificates to each other.
Now, in the Palo Alto firewall, we either generate a self-signed certificate or generate a CSR. In this example, I am using a self-signed certificate for SSL Decryption. Now, the same certificate will be installed on all client machines. So, all web traffic generated by the client machines will be encrypted by the same certificate. In this scenario, there will be two times SSL handshakes happen. First from Client to the PA Firewall and the second one is between the Firewall and the actual destination. So, the Firewall will decrypt all SSL traffic generated by the client machine and re-encrypt it than send it to the actual destination. Therefore, the firewall can perform a deep inspection of all encrypted web traffic.
How to configure SSL Decryption on Palo Alto Firewall
To configure SSL Decryption on the Palo Alto firewall, we either generate a self-signed certificate or generate a CSR. In this example, I am using a self-signed certificate for SSL Decryption. After the Certificate generation, we need to configure the security policy for SSL Decryption on the Palo Alto Firewall and at last, we need to install the same certificate on the Client machine. So, let’s first understand the network topology and start configuring the SSL Decryption on the Palo Alto firewall.
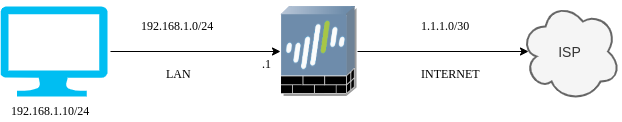
So, In this example, I have my LAN subnet 192.168.1.0/24 and the Internet subnet is 1.1.1.0/30. In the LAN segment, I have my test machine which has 192.168.1.10 IP address. So, we will decrypt all the encrypted traffic from the 192.168.1.10 IP address. Let’s start!
Step1: Generating The Self-Signed Certificate on Palo Alto Firewall
Access the Device >> Certificate Management >> Certificates and click on Generate. Now, provide a Friendly Name for this certificate. In the Common Name field, type the LAN Segment IP address i.e. 192.168.1.1. Check the mark (√) just before the Certificate Authority. You can also define the Certificate Attributes, but for the SSL Decryption, we didn’t require these attributes.
More Reading on: Self-Signed Root CA certificate in Palo Alto Firewall
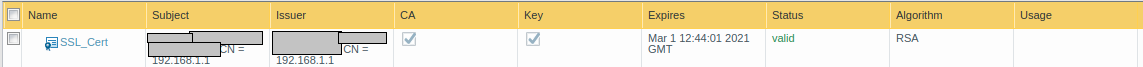
Step 2: Configuring the certificate as “Forward Trust” and “Forward Untrust”
It is always recommended that you should configure two different certificates during the SSL Decryption configuration. But, in this example, I generated only one certificate. To make SSL Decryption working, we need to configure the same certificate as “Forward Trust” and “Forward Untrust”. So, let’s click on the same certificate and click on All the checkbox options as shown in the picture below.

Step 3: Configuring the SSL Decryption Policy on Palo Alto Firewall
It is always recommended to not decrypt some URL Categories such as Financial Services & Health and medicine, as users may consider this an invasion of privacy. Decryption Rules are evaluated in order, so you can write multiple rules. The firewall will follow top to down approach while evaluating the policy.
Now, we need to configure the SSL Decryption on Palo Alto Firewall. Just access the Policies >> Decryption >> and Click on Add. In the General tab, provide the Name for this policy.
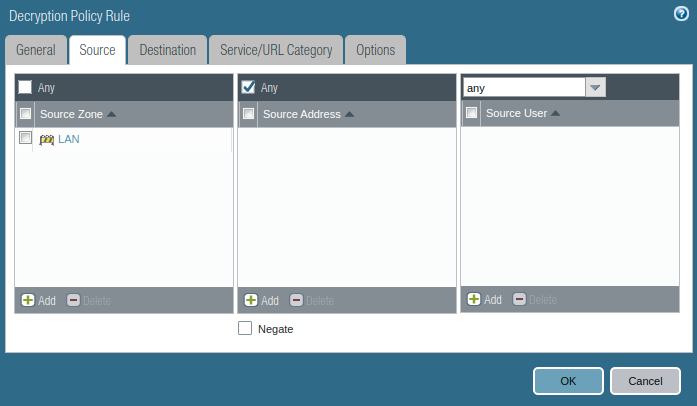
In the Source Tab, provide the Source Zone & Source IP Address.
Now, In the Destination Tab, provide the Destination Zone and leaves the Destination Address field to any.
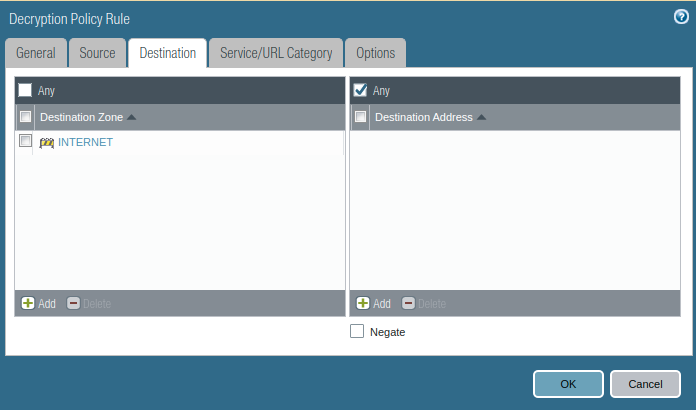
You can specify the application/services as per your requirements. Let’s continue by keeping any-any in both Applications and Services.
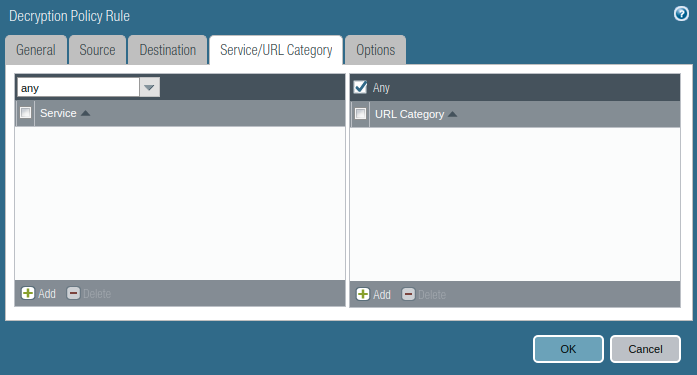
Last, in Options Tab, check the Decrypt radio button. In this Type filed, select the SSL Forward Proxy. Keep the Decryption Profile to None.
Let’s summaries our SSL Decryption Policies. We configure two different policies in the same way as shown above. Notice, In the first rule, I have selected No-Decrypt options for Financial-Services & Health-and-medicine. However, it only works if you have URL Filtering Licence on Palo Alto Firewall.

Step 4: Configuring the SSL Decryption Response Page (Optional)
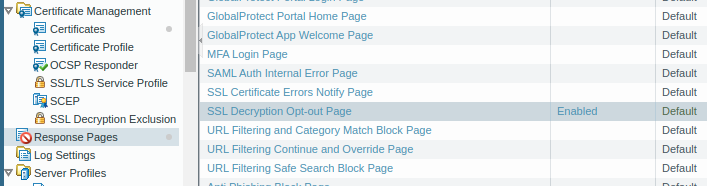
Whenever a user initiates HTTPS traffic, the firewall sends a response page that your secure SSL connection is decrypted by the firewall. So, users can be notified that their SSL connection being decrypt. It can be enabled via the Response Pages. Access the Device >> Response Pages >> and Enable the SSL Decryption Opt-out Page.
Step 5: Exporting the Certificate from the Firewall and Importing it on Client machine browser
In this example, we are using a Self-Signed Certificate for SSL Decryption. So, we need to export the certificate and install it to the Client browsers (i.e. Chrome, Firefox, etc). So, let’s access the Device >> Certificate Management and select the Generated Certificate and click on Export. You need to export the certificate in the following way, so it will be easy to install it on the Client browser.
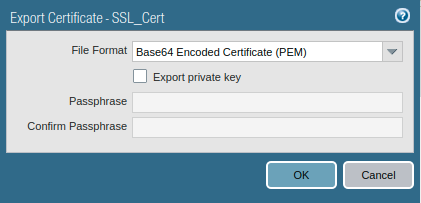
Now, you need to install the same certificate on the client machine browser. For Internet Explorer, you just need to right-click on the certificate and you need to install it. For Firefox, you need to open the browser and access the certificate settings.
Step 6: Commit all the changes on the Palo Alto Firewall
Now, we have done the SSL Decryption configuration on the Palo Alto firewall. Let’s commit to making these changes affect take place. So, click on the “Commit” button right-hand upper corner to commit our changes.
Step 7: Accessing the HTTPS web traffic and Verifying the SSL Decryption
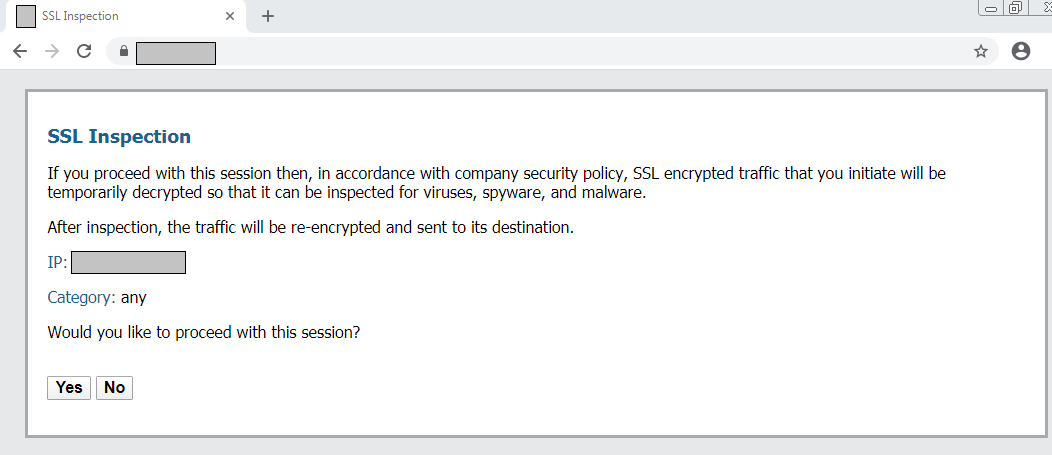
Now, let’s test our configuration by accessing any website (Secure HTTP). Since we enable the SSL Decryption Response Page in Step 4, users may get the response page as shown below.
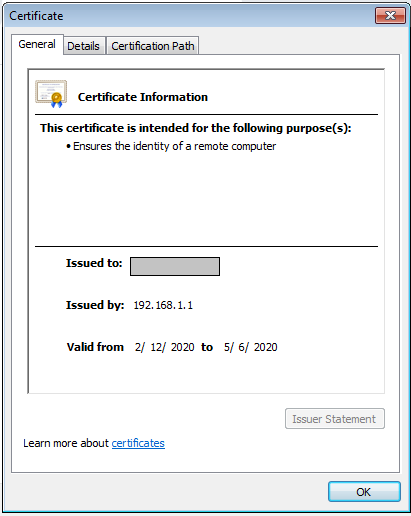
Once, you access any website, you will be shown Lock Icon on browser top corner. You need to check which certificate is used by the browser while accessing the website. If this is the same certificate you imported in Step 5, then SSL Decryption is working perfectly.
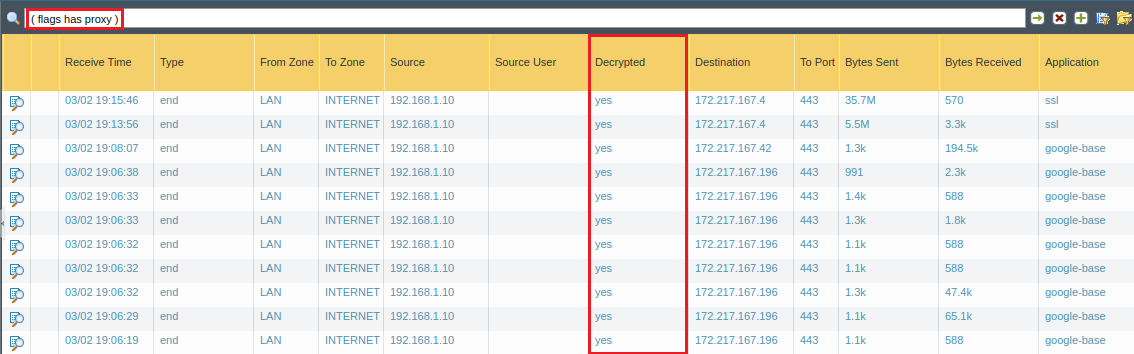
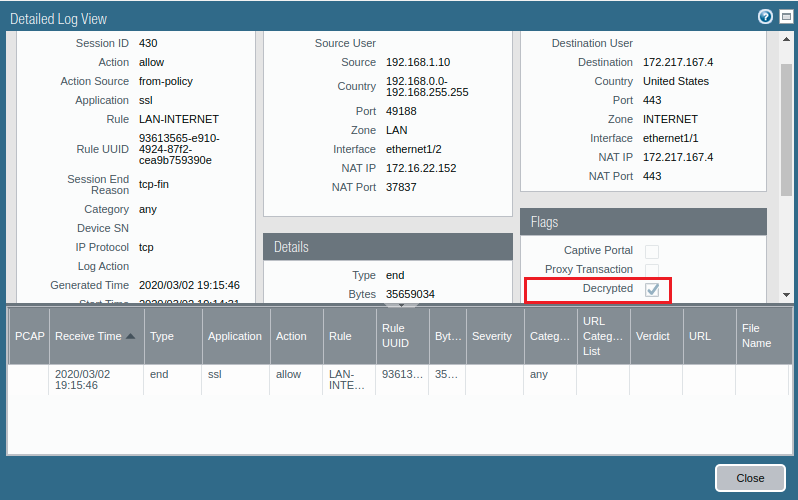
Alternatively, access the Monitor >> Logs >> Traffic on Palo Alto Firewall. Filter the logs by ” ( flags has proxy )” filter. All of your traffic that matches this filter is decrypted. You can click on Magnifying Glass to verify it.
Related Articles
- Clientless VPN on Palo Alto Firewall
- How to Generate Self-Signed Root CA certificate in Palo Alto Firewall
- Captive Portal in Palo Alto Firewall
- How to configure GlobalProtect VPN on Palo Alto Firewall
References
Summary
In this article, we discussed SSL Decryption. For the deep inspection on HTTPS (Encrypted Web Traffic) Traffic, we need SSL Decryption. You need either a self-signed certificate or a certificate that is signed by an external certificate authority for the SSL Decryption. We used a self-signed certificate for SSL Decryption. We configure the Decryption policy on the Palo Alto firewall. Before the testing, we enabled the response page for the SSL Decryption on the Palo Alto firewall. At last, we check the logs for the SSL Decryption.
Did you like this article? Please let me know if you facing any issue during SSL Decryption.
Your tips is amazingly significant.
Thanks, @JamesFag! Glad to know that it is useful.
Si uso un certificado firmado por una autoridad de certificación externa tambien necesito instalarlo en la máquina cliente final?
Just testing and found an interesting situation:
For security reasons you want to decrypt all traffic user and servers. You want to notify users about this so you enable SSL decryption Opt-Out page. But you aren’t able to enable this for users so for specific subnet and not enable this feature for specific subnet. Only solution I see is to use basic captive portal.