In this article, we will configure the IPSec tunnel between the Cisco ASA and Cisco Router. We will configure the Policy Based IPSec tunnel between both of them. You must have static routable IP addresses to establish the IPSec tunnel. IPSec tunnel allows you to send or receive encrypted traffic to the remote site over the Internet. So, let’s start!
Scenario – How to Configure IPSec VPN between Cisco ASA and Cisco Router
In this example, I have a Cisco ASA firewall and Cisco Router. Both Cisco ASA and Router have static routable IP addresses. Cisco ASA has two different zones i.e. Outside and Inside. The outside network is 1.1.1.1/30 and the Inside network is 192.168.1. On the other hand, Cisco Router (R1) connected with ISP using a 2.2.2.2/30 subnet. The LAN subnet of the remote network is 192.168.2.0/24.

So, Let’s start the configuration by checking the connectivity between both the devices.
[terminal]ciscoasa# ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/28/30 ms[/terminal]
Configuring the IPSec Tunnel on Cisco ASA
First, we will configure the IPSec Tunnel on Cisco ASA Firewall. Although, you can configure the IPSec tunnel on the Cisco Router first :).
We need to configure the following steps to configure IPSec on Cisco ASA:
- Configuring the Phase1 (IKEv1)
- Defining the Tunnel Group and Pre-Shared Key
- Configuring the Phase2 (IPSec)
- Configuring the Extended ACL and Crypto Map
So, let’s start the configuration by configuring the Phase1 of Cisco ASA. Access the global configuration mode of Cisco ASA and start with below commands:
Configuring the Phase1 (IKEv1) on Cisco ASA
[terminal]ciscoasa(config)# crypto ikev1 policy 10
ciscoasa(config-ikev1-policy)# encryption 3des
ciscoasa(config-ikev1-policy)# hash md5
ciscoasa(config-ikev1-policy)# authentication pre-share
ciscoasa(config-ikev1-policy)# group 2
ciscoasa(config-ikev1-policy)# lifetime 86400
ciscoasa(config-ikev1-policy)# exit[/terminal]
Now, let’s understand the meaning of each command.
- Encryption: 3des (It is used to encrypt the Phase1 traffic).
- Hash: md5 ( md5 is a hashing algorithm. It authenticates our data using Hash)
- Group: 2 (Diffie Hellman Group 2)
- Authentication: In this example, we are using the pre-shared key as authentication)
- Lifetime: 86400 ( Default lifetime for the Phase1)
In the Cisco ASA, we need to enable the Crypto IKEv1 to the Internet-facing interface. So, we can do this using the below command:
[terminal]ciscoasa(config)# crypto ikev1 enable outside[/terminal]
Configuring the Tunnel Group and Pre-Shared Key on Cisco ASA
Now, we need to define the tunnel interface and the Pre-Shared Key. In this article, I’m using GNS3Network as a pre-shared key.
[terminal]ciscoasa(config)# tunnel-group 2.2.2.2 type ipsec-l2l
ciscoasa(config)# tunnel-group 2.2.2.2 ipsec-attributes
ciscoasa(config-tunnel-ipsec)# ikev1 pre-shared-key GNS3Network
ciscoasa(config-tunnel-ipsec)#exit[/terminal]
Configuring the IPSec IKEv1 Phase2
Here, we need to define the Encryption and Authentication methods for IPSec Phase2.
[terminal]ciscoasa(config)# crypto ipsec ikev1 transform-set TSET esp-3des esp-md5-hmac[/terminal]
Now, let’s quickly understand this command.
- ESP: ESP Stands for Encapsulating Security Payload and it’s an IPSec Protocol
- 3DES: 3DES is one of the Encryption Algorithm
- MD5: MD5 is a Hashing algorithm, which is used to maintain the data integrity
Configuring the Crypto MAP and Extended ACL to allows IPSec traffic on Cisco ASA
This is the final step of our configuration. Here, we need to define an Extended ACL to allow the traffic. Also, here we need to configure the Crypto MAP and call the configured crypto map to the External Interface. I am configuring two address-objects to simplified the Access Control List (ACL).
Address Object and Extended ACL to allows traffic
[terminal]ciscoasa(config)#object-group network local-network
ciscoasa(config-network-object-group)#network-object 192.168.1.0 255.255.255.0
ciscoasa(config-network-object-group)#object-group network remote-network
ciscoasa(config-network-object-group)#network-object 192.168.2.0 255.255.255.0
ciscoasa(config-network-object-group)#access-list IPSec_Traffic extended permit ip object-group local-network object-group remote-network[/terminal]
Configuring the Crypto MAP
[terminal]ciscoasa(config)# crypto map CMAP 10 match address IPSec_Traffic
ciscoasa(config)# crypto map CMAP 10 set peer 2.2.2.2
ciscoasa(config)# crypto map CMAP 10 set ikev1 transform-set TSET[/terminal]
Enabling the Crypto MAP on Outside Interface
[terminal]ciscoasa(config)# crypto map CMAP interface outside[/terminal]
We have done the configuration of IPSec Tunnel on Cisco ASA. Now, we will configure the IPSec on Cisco Router.
Configuring the IPSec Tunnel on Cisco Router
As we already described all the parameters used in the IPSec tunnel. So, we will configure all the configurations on the remote router R2.
Configuring the Phase 1 on the Cisco Router R1
Here, we need to configure the IKEv1 or Phase 1 on the Cisco Router. Just access the global configuration mode of the Cisco Router and follow the below commands.
Note: All the configuration of Phase1 should be same as Cisco ASA.
[terminal]R1#configure terminal
R1(config)#crypto isakmp policy 1
R1(config-isakmp)# encryption 3des
R1(config-isakmp)# hash md5
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 2
R1(config-isakmp)# lifetime 86400[/terminal]
[terminal]R1(config)#crypto isakmp key Gns3Network address 1.1.1.1[/terminal]
Phase 2 configuration on the Cisco Router R2
Just, access the global configuration mode of the Cisco Router and follow the below command:
Note: All the configuration of Phase2 should be same as Cisco ASA.
[terminal]R1(config)#crypto ipsec transform-set TSET esp-3des esp-md5-hmac[/terminal]
Configuring the Extended ACL and Crypto MAP
Here, Extended ACL will allow the traffic from the Local Subnet i.e. 192.168.2.0/24 to the remote subnet i.e. 192.168.1.0/24.
[terminal]R1(config)#ip access-list extended IPSEC_List
R1(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255[/terminal]
Now, we need to configure the Crypto Map using the Extended LIst (ACL) and Transform Set (IPSec Phase2).
[terminal]R1(config)#crypto map CMAP 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.R2(config-crypto-map)#set peer 1.1.1.1
R1(config-crypto-map)#set transform-set TSET
R1(config-crypto-map)#match address IPSEC_List[/terminal]
Now, Just set the Crypto Map to the outside interface.
[terminal]R1(config)#interface FastEthernet 0/0
R1(config-if)#crypto map CMAP
*Jan 13 21:26:41.991: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON[/terminal]
Hey! we finished the configuration of the IPSec tunnel on the Cisco Router as well as Cisco ASA. Now, we need to test the configuration by initiating some traffic towards the remote network.
Testing the IPSec tunnel by initiating the traffic from Cisco ASA
As we have finished the configuration of the IPSec Tunnel between the Cisco ASA and Cisco Router. Now, we need to initiate the traffic either from Cisco Router or Cisco ASA firewall to make tunnel up and run. Here, I access the CLI of the Cisco ASA Firewall and initiate some traffic towards the Cisco Router LAN Subnet, i.e. 192.168.2.0/24.
[terminal]ciscoasa# ping inside 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
?!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 30/30/30 ms[/terminal]
The first packet is dropped just because of the ARP request and response. No further packet will be dropped.
Optional: If you are tryining to initiate the traffic from Cisco ASA Interface IP, you need to allow the management access towards the subnet.
[terminal]ciscoasa(config)# management-access inside [/terminal]
Troubleshooting the IPSec tunnel
In this part of this article, we will discuss some basic commands, which helps you to troubleshoot the IPSec tunnel which is configured between the Cisco ASA and Cisco router.
On the Cisco Router
[terminal]R1#show crypto session
Crypto session current status
Interface: FastEthernet0/0
Session status: UP-ACTIVE
Peer: 1.1.1.1 port 500
IKE SA: local 2.2.2.2/500 remote 1.1.1.1/500 Active
IPSEC FLOW: permit ip 192.168.2.0/255.255.255.0 192.168.1.0/255.255.255.0
Active SAs: 2, origin: crypto map[/terminal]
[terminal]R1#show crypto map
Crypto Map “CMAP” 10 ipsec-isakmp
Peer = 1.1.1.1
Extended IP access list VPN-TRAFFIC
access-list VPN-TRAFFIC permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
Current peer: 1.1.1.1
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
TS: { esp-3des esp-md5-hmac } ,
}
Interfaces using crypto map CMAP:
FastEthernet0/0[/terminal]
[terminal]R1#show crypto isakmp key[/terminal]
[terminal]R1#show crypto isakmp peers[/terminal]
[terminal]R1#show crypto isakmp policy[/terminal]
[terminal]R1#show crypto ipsec transform-set[/terminal]
On the Cisco ASA Firewall
[terminal]ciscoasa# show running-config ipsec[/terminal]
[terminal]ciscoasa# show running-config crypto ikev1[/terminal]
[terminal]ciscoasa# show running-config crypto map[/terminal]
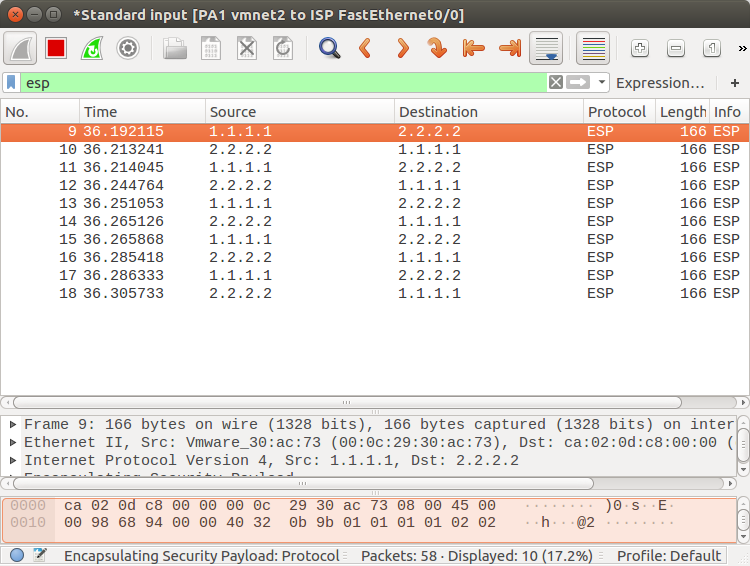
Analyzing the IPSec traffic through the Wireshark
During the configuration of the IPSec Phase2, we defined ESP (Encapsulating Security Payload) as the IPsec protocol, so all the real traffic which goes towards the peer end will be encrypted using this protocol. So, you will only find ESP packets in the packet capture as shown below.
Related Articles
- IPSec Tunnel Between Cisco Routers | Site to Site VPN Between Cisco Routers
- How to configure IPSec VPN between Palo Alto and FortiGate Firewall
- How to configure GRE Tunnel between Cisco Routers
Reference
Summary
In this article, we configure the IPSec tunnel between the Cisco Router and Cisco ASA Firewall. We also discussed the Encryption and Authentication algorithms. However, you must need static routable IP addresses to configure the IPSec VPN between two remote networks.
Hope you like this article! Please let us know if you need further help regarding the IPSec tunnel.